Content Security Policy
A Content Security Policy (CSP) can greatly reduce the risk and impact of XSS and other code injection attacks in browsers. It defines an HTTP header that allows the creation of a whitelist of trusted content sources and instructs the browser to only execute or render resources from those sources.
So, if the following error appears in the console on your site -
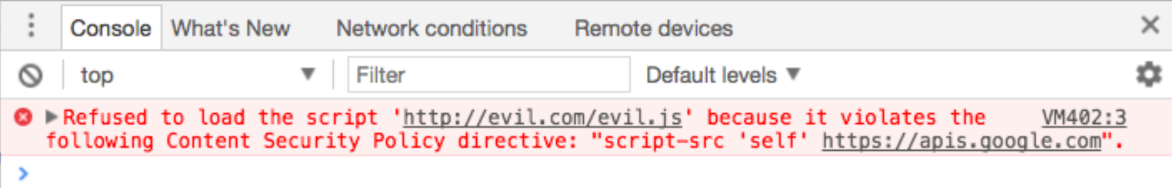
- it means that instead of downloading the script from this source, the browser blocked it.
More information on this error can be found in this article.
An example of an error you may receive when using Dashly:
Refused to connect to 'wss://realtime-services.dashly.app/websocket/...' because it violates the following Content Security Policy directive: "default-src https:". Note that 'connect-src' was not explicitly set, so 'default-src' is used as a fallback
It means that the wss protocol, which is required for the chat to work, is not allowed in the Content Security Policy settings.
If CSP is configured on your site, then you need to add the policy as follows in order for our services to work:
script-src https://*.dashly.app 'unsafe-inline' 'unsafe-eval'; style-src https://*.dashly.app 'unsafe-inline'; img-src https://*.dashly.app; font-src https://*.dashly.app; connect-src https://*.dashly.app https://*.dashlytrack.app wss://*.dashly.app; media-src https://*.dashly.app;
If you have a Calendly integration configured, then add this to your policy as well:
script-src https://assets.calendly.com; style-src https://assets.calendly.com; frame-src https://calendly.com;
When the policy is updated, the error will disappear and everything will work correctly.
